EXECUTIVE SUMMARY
GMoney is a platform facilitating the loan transactions between the borrowers and the NBFCs/Banks. All loan applications are approved and sanctioned by NBFCs/Banks registered with RBI and communicated upfront during Loan application.
The Platform provides access to an online platform bringing together consumers, financial institutions, data partners and other partners willing to abide by their respective Terms & Conditions. GMoney’s lending partners provide various kinds of medical loan products as specifically supplied by the Users through the Platform.
THE CLIENT’S CHALLENGE
Client is using WordPress and if we start using wordpress plugins for application layer security, it slows down the website. Also as a nature of the category and known WordPress vulnerabilities, hackers try out their attacks on websites like GMoney.
WordPress faces several challenges in terms of infrastructure and security. The platform’s infrastructure is hosted on AWS EC2, leveraging the auto scaling feature for enhanced scalability. This enables the system to handle high levels of traffic efficiently. However, one significant challenge lies in effectively segregating malicious traffic from legitimate traffic. The infrastructure must be capable of distinguishing and filtering out malicious elements to ensure uninterrupted transactional workflows and prevent interference.
Moreover, WordPress struggles with safeguarding the website against individuals or groups aiming to disrupt releases. These culprits pose a constant threat, and defending against their malicious intentions has become a prominent challenge for the platform. Implementing robust security measures and continuously monitoring for potential vulnerabilities are crucial aspects of combating these hindrances effectively.
SOLUTION
After exploring various solutions, packages, and services, we thoroughly tested numerous options available to us. Among them, AWS WAF proved to be the most suitable and cost-effective solution for securing clients WordPress website.
AWS WAF offers a comprehensive set of rules designed to protect clients’ systems from potential vulnerabilities specific to WordPress. These rules are regularly updated to address emerging threats and new vulnerabilities, ensuring that client’s website remains secure.
One of the key features of AWS WAF which Techpartner insists to configure is its ability to track and monitor the IP addresses associated with malicious or fake traffic. This functionality enables clients to easily block unwanted IP addresses and conduct thorough investigations on non-proxy IP addresses. By identifying competitor agencies and known culprits, we can take appropriate measures to safeguard client’s websites against potential threats.
The Techpartner team demonstrated that AWS WAF is seamless and does not require any modifications to clients’ Google Analytics setup. The security layer of AWS WAF operates independently without compromising the performance of our website. This ensures that clients’ websites remain both secure and efficient.
Furthermore, AWS WAF offers a comprehensive collection of signatures and rules that we can readily access and present to our clients. This transparency allows us to demonstrate the robust security measures in place, instilling confidence in our clients and reinforcing our commitment to protecting their data.
Overall, AWS WAF emerges as the ideal choice for safeguarding a client’s WordPress website, providing a powerful combination of effective security measures, effortless implementation, and valuable insights for both our team and our customers.
INSIGHT TO ACTION
The AWS WAF was set up with a web access control list (web ACL), a set of rules that enables, blocks, or tallies web requests based on customizable web security rules and conditions that were predefined. Its primary function is to shield WordPress against typical web exploits that could impact workload availability and performance, jeopardize security, or consume excessive resources.
To customize the WAF, we utilized a combination of AWS’s pre-defined rules and wrote custom rules to safeguard the customer environment against attacks that are unique to the region or workload.
PROPOSED ARCHITECTURE
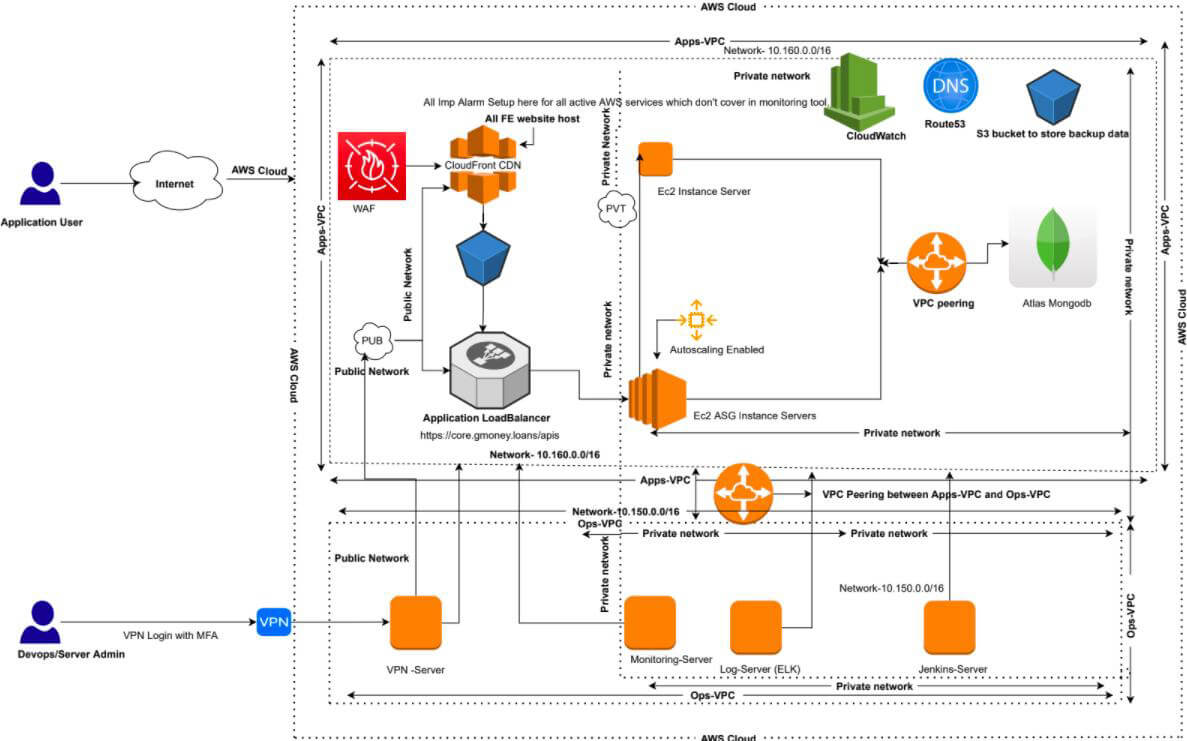
BENEFITS
- Ease of integration of AWS WAF with client’s existing application.
- Data Transfer cost reduced by 15% after implementing AWS WAF as the direct reference to S3 objects now handled by AWS WAF + CDN combined.
- Client saw the security posture improvement in terms of reduced in the number of Vulnerability/incidents.
AWS STACK
- AWS WAF
- AWS CloudFront
- AWS Application Load Balancer (ALB)
- AWS EC2 Auto Scaling Groups (ASG)
- AWS Cloudwatch
- AWS Route53
- AWS S3
- AWS CodeBuild
- AWS CodeDeploy
- AWS Lifecycle Manager
- AWS RDS (PostgreSQL)
- AWS KMS



